Phishing attacks typically stoke greed or fear, just as many genuine business pursuits do.
Not surprisingly, they enjoy a fairly high success rate. At 3%, it comes close to the conversion rate of leading ecommerce websites like Amazon and Flipkart.
Surprised to learn that phishing emails have a success rate of ~3%. That's as high as the conversion rates of leading ecommerce websites e.g. Amazon (4%), Flipkart (2%). https://t.co/ssVG6ThUlE via @walrusmagazine .
#Con #Scam— Ketharaman Swaminathan (@s_ketharaman) March 16, 2020
We contended in All Deceptions Are Not Equal – Bait-And-Switch Versus Phishing that it’s hard to spot phishing attacks.
That problem has now escalated to the next level, thanks to the multitude of variants of phishing attacks that I’ve come across lately.
- Genuine stuff looks like phishing
- Phishing passes off as genuine stuff
- Shortened and vanishing links
- Misleading SMS Headers
- Brick-and-mortar phishing
Let’s get down to it.
#1. Genuine stuff looks like phishing
Take this leading private sector bank in India that used to call itself the most valuable bank in the world until I pointed out that it wasn’t even among the 20 most valuable banks in the world, after which it changed its story to “most expensive bank stock in the world”, which has also become a dubious claim with flatlining of its stock price in the last two years.
It regularly sends out emails from weird email addresses e.g. info@e.addsdigital.com.
@gtm360: Judging by sender’s address (info@e.addsdigital.com), this email looks dodgy. But I found out that this is a genuine email from a genuine subsidiary of HDFC Bank called HDB Financial Services. It’s becoming hard to distinguish between genuine and phishing emails these days.
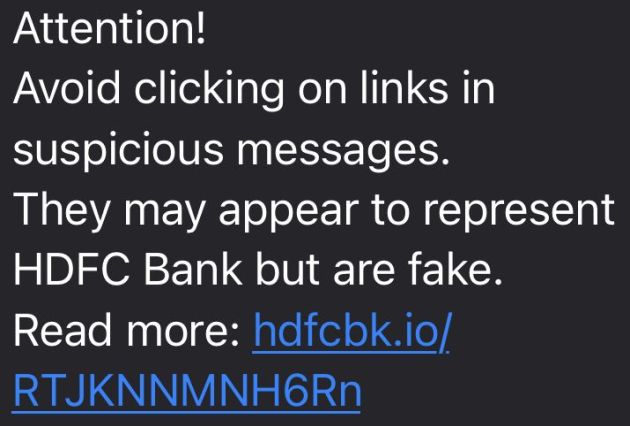
This bank recently sent out an SMS warning recipients not to click on suspicious links masquerading as the bank’s and then invited them to learn more by clicking – wait for it – hdfcbk.io/RTJKNNMNH6Rn. (Source: Twitter)
The bank missed the irony that people who heed such warnings would find this link terribly suspicious. (“What me worry” people would ignore this message anyway.)
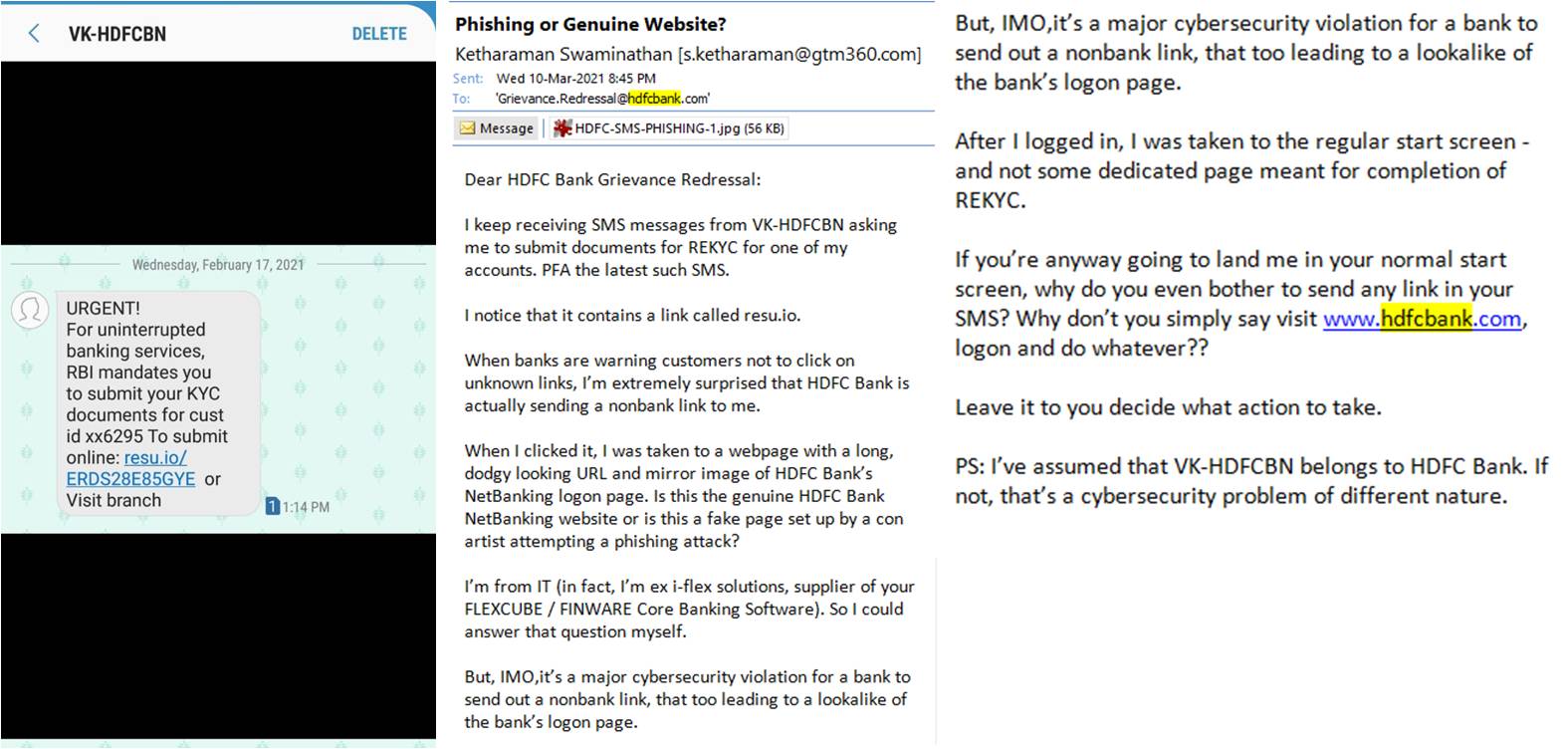
I once received an SMS from this bank, asking me to complete my RE-KYC by clicking on resu.io, a link that had no obvious connection with the bank’s website. I inquired with the bank’s grievance redressal cell whether this link was genuine or fake.
In all these cases, the communications were genuine but looked like phishing attempts.
#2. Phishing passes off as genuine stuff
Long time readers of this blog would recall that Mint asked users to enter their online banking credentials on its website. While that stopped me dead in my tracks, close to 10 million people went ahead. The PFM pioneer was soon acquired by Intuit for $170 million in the late oughties.
Ten years later, you’d think methods to access bank accounts would have become more secure.
You’d be wrong. Take Plaid for example.
The leading aggregator of banking data helps fintechs to access their customers’ bank accounts.
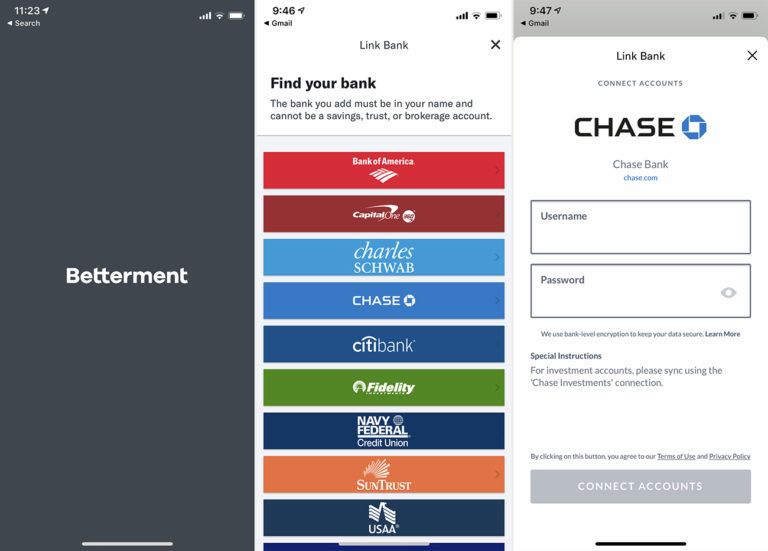
Let’s see how it does that by taking the case of Betterment and JP Morgan Chase. For the uninitiated, Betterment is a leading wealth management fintech in USA and JP Morgan Chase is America’s largest bank.
Per Ben Thompson @ Stratechery, customers install the Betterment app, then click a button to link it to their bank account. Plaid kicks in and displays the logos of leading banks in USA. Once the user clicks the Chase logo, Plaid shows them a screen that looks exactly like JPMC’s NetBanking login but is not the real JPMC login screen! Users enter their JPMC online banking userid and password on this look-alike screen created by Plaid. Plaid saves the credentials, and uses them to access the user’s JPMC bank account going forward.
When tout does it at Ambar Oscar Minor, it's Blackmarketing. When StubHub does it, it's Premium. When Nigerian Prince does it, it's Phishing. When Plaid does it, it's Account Aggregation. Becoming 1%ers is less about Product, more about Packaging, Jargon, Obfuscation. https://t.co/tcz7fsso98
— Ketharaman Swaminathan (@s_ketharaman) April 11, 2020
The access mechanisms of Mint and Plaid are canonical examples of phishing but, since customers and / or regulators don’t seem to care, they pass off as genuine.
#3. Shortened and vanishing links
As we saw in All Deceptions Are Not Equal – Bait-And-Switch Versus Phishing, it’s hard enough to figure out by visual inspection which of the following hyperlinks is genuine and which is phishing:
- paypal.xyz.com
- xyz.paypal.com
The task becomes impossible when the links are shortened:
- http://ow.ly/xtMO30s2UM5
- http://ow.ly/Qmwn30s2UMl
Ditto when you click the link and it vanishes after a few seconds.
Beware of shortened & rapidly-vanishing URLs in emails purportedly sent by LI, FB, PayPal, etc. They seem to be new phishing techniques!
— Ketharaman Swaminathan (@s_ketharaman) September 9, 2013
Ergo, when somebody receives shortened or vanishing links, it’s virtually impossible for them to figure out whether it’s genuine or phishing.
#4. Misleading SMS Headers
I don’t expect the average reader of this blog to have seen, let alone used, a telex machine but the go-to communications machine before the Internet had something called key. Appearing at the start of every telex message, the key authenticated the sender of the message to its receiver. It was unbrakeable and could be used as evidence of sender in a court of law. Ergo, telex was used as a secure way to carry out realtime fund transfers between banks. Ergo the term TT (Telex Transfer aka Wire Transfer).
Unlike telex, neither SMS (nor email) supports the concept of Verified Sender ID.
Ergo, when you get a text, you need to look at the SMS Header and use your general knowledge / common sense to decipher who the sender of the message is e.g. “TM-HSBCIM? Ah it must be HSBC Bank”; “VK-GODDY must be Go Daddy”; and so on.
This works well – until it doesn’t.
BP-RTODPT is not RTO Department (DMV of India). This SMS Header belongs to a motor insurance company that uses the bait-and-switch dark pattern to sell you a policy that you don’t need.
Yet another requirement for "TrueCaller for SMS Sender" app: Fraudster uses SMS Sender Heading QP-ITDEPL to masquerade as Income Tax Department and carry out an Income Tax Refund phishing scam. pic.twitter.com/rBmIV0c2KH
— Ketharaman Swaminathan (@s_ketharaman) January 23, 2020
Then there’s QP-ITDEPL, the header used by a scamster to send out texts about income tax refund. A poor sucker who got this SMS thought it was from the Income Tax Department, took the offer for refund to be genuine, clicked through the link, and lost INR 2.94 Lakhs ($3900) in the bargain.
#5. Brick-and-mortar phishing
Phishing has spread beyond the digital world.
Somebody allegedly set up a fake branch of State Bank of India, India’s largest bank, and collected deposits from unsuspecting walk-in customers.
OMG. Never thought anyone would attempt a brick-and-mortar phishing attack. #SBI https://t.co/tNhNGPNP0H
— Ketharaman Swaminathan (@s_ketharaman) July 11, 2020
Recently one guy landed up at my doorstep and claimed to be the new Relationship Manager from my bank. When he started asking all kinds of personal questions, I sent him away.
@s_ketharaman: Out of the blue, a guy landed up on my doorstep. Claiming to be my new RM from HDFC Bank, he asked me if I had any issues with my account. Has @HDFC_Bank started making house calls without appointments? Or was this a physical world “phishing” attempt??
Now, this could be a phishing attempt in the real world or a genuine attempt on the part of my bank to solve my frequent complaints about the multitude of people who contact me via email and telephone claiming to be my relationship manager.
I have no way to know.
Variants are making phishing attacks more lethal than ever before. Traditional tips to safeguard against them are not working any more.
We need rigorous tests to spot phishing. Good news is, unlike verification services for fake news, professionally-developed tests for identifying phishing can be foolproof.
Yet another phishing attack.
Yet another case of money lost to Business Email Compromise.
Yet another set of well-meaning but eventually useless precautions.
The only precaution you need is "sub-dollar pipecleaning deposit" followed by "out-of-band confirmation". pic.twitter.com/AoocDcY0UP— GTM360 (@GTM360) February 13, 2022